 LibreCrypt: Open-Source disk encryption for Windows
LibreCrypt: Open-Source disk encryption for Windows
 LibreCrypt: Open-Source disk encryption for Windows
LibreCrypt: Open-Source disk encryption for Windows
A "keyfile" is a small file (about 512 bytes) which can optionally be created for a LibreCrypt, and contains the information required to open it. Keyfiles are encrypted with a password, which must be given in order to use the keyfile.
More than one keyfile can be created for the same container.
Keyfiles are useful as they allow critical information which is required in order to open a Container to be stored separately to the container which they relate to; on a floppy disk, or USB drive, for example - which would be too small to store the entire LibreCrypt on. In this way, your container may be stored on your computer, but the information required to access it can be stored in a physically more secure location (e.g. in a locked safe)
Keyfiles may be used for password recovery, or to reset forgotten passwords. When confidential information is held within a container, a keyfile can be created for it and stored in a safe location. Should the employee which normally uses the container be unavailable, or cannot remember the container's password, it can still be opened using a keyfile that has was previously created for it (together with that keyfile's password) - even if the container's password has been subsequently changed.
Keyfiles may also be used to provide multiple users with access to open and use the same container; each using a password of their own choosing.
Note: Keyfiles are specific to the container they are created for! Although a keyfile for one container may be able to successfully open another container, the virtual drive shown will appear to be unformatted - the files within the container will remain securely encrypted and unreadable.
To create a new keyfile, select "Tools | Create keyfile..." to display the "keyfile wizard", which will guide you through the process in a series of simple steps.
The process of opening a container using a keyfile is identical to the normal open procedure, with the exceptions that:
As well as containers in files, you can also encrypt partitions, and even entire disks, by selecting "Partition/disk" when prompted during the container creation process.
It is not recommended that inexperienced users do this - is the kind of operation that should only be carried out by those who are familiar with disk partitioning and understand what they're doing.
It is extremely important that you make absolutely sure you have selected the correct disk/partition to be used when creating a new partition based container!
Making a container will overwrite the first 512 bytes of the selected partition (or start of the disk, if using the entire disk). In addition if 'overwrite with chaff' is enabled, the entire partition will be overwritten.
If the 'overwrite with chaff' option is enabled, it is not possible to recover any data on the drive after making the container.
If this option is disabled, you may be able to revert the changes LibreCrypt makes to your partition/disk if the first 512 bytes have ben backed up ("Tools | Critical data block | Backup...").
Note: Such a backup will be of less use after the container created has been used, since this will carry out further overwrites to the partition/disk.
Ideally, you should backup your entire system before creating encrypted partitions, just to be on the safe side - though this may not be practical.
The partition display shown by LibreCrypt will give more information about the partitions on a disk (e.g. drive letters allocated, size of partitions, proportional display) when used by a user with administrative privileges. A user with normal privileges will be shown less information due to their restricted access rights.
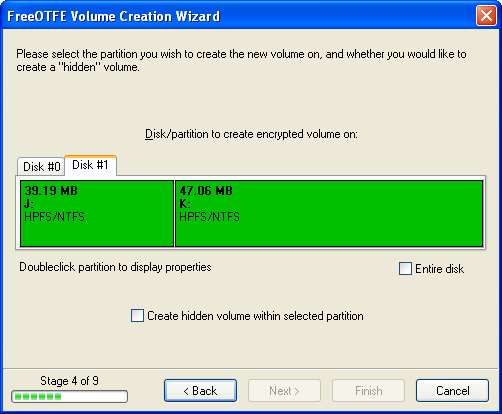 New container wizard showing full partition information
New container wizard showing full partition information
Therefore, it is recommended that you create any new partition based containers while logged in as an administrator. To do this under Windows Vista and above, you will need to run LibreCrypt with elevated permissions: locate the "LibreCrypt.exe" executable where you installed it, rightclick on this executable and select "Run as administrator" from the context menu.
In order to format a new partition or disk based Box under Windows Vista x64 (64 bit), the container must be opened while LibreCrypt is running with elevated permissions.
To do this:
This procedure only needs to be carried out once in order to format the container; it may subsequently be opened and used by any user.
Elevated permissions are not required to format file based containers.
LibreCrypt offers users the ability to create "hidden Containers" stored inside other "outer" Containers.
To create a hidden container:
To open your hidden container, proceed as if opening the outer container, but when prompted to enter your password, click the "Advanced" button and enter the offset. (See the section on advanced password entry options). The 'default hidden offset' may be retrieved at any time by opening the outer container and right-clicking -> properties.
If you enter a custom value for the offset, make sure you remember it! For security reasons, LibreCrypt doesn't store this information anywhere, and so you will have to enter the same offset into the password entry dialog every time you wish to open your hidden container.
More than one hidden container can be stored within the same host container, by using different offsets
Warning:Once a hidden container has been made, subsequently saving data to the outer container can corrupt the hidden container, and destroy its data. It can also change the default hidden offset.
Once created in this way you should only open the outer container as read-only, and never save any files to the outer container.
Please see the Plausible Deniability section for further information on the practical uses and considerations of hidden Containers.
At the end of the New container process, LibreCrypt will display a summary of the container it is about to create. At this stage, more advanced options be configured for the new container, by selecting the "Advanced..." button.
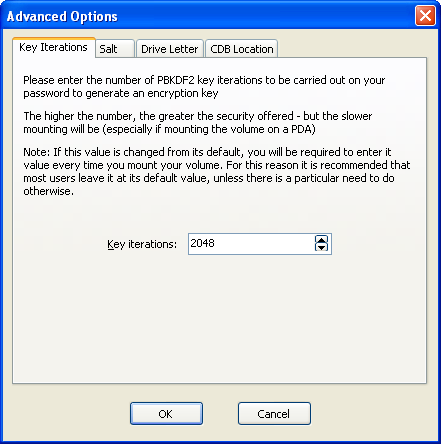
_Advanced container creation options_
Before the user's password is used to encrypt/decrypt the CDB, it is processed using PBKDF2 to increase security.
This tab allows the number of PBKDF2 iterations to be set by the user; higher values increase security, but will also increase the amount of time taken to open the container.
The default number of key iterations is 2048.
Before the user's password is used to encrypt/decrypt the CDB, it is processed using PBKDF2 to increase security.
Part of this processing involves the use of a random "salt" value, which reduces the risk of dictionary based attacks. This tab allows the length of the salt value (in bits) to be set by the user.
It should be noted that to open a container which has a non-default (256 bit), you MUST specify the correct salt length by using the "Advanced" options available on the LibreCrypt password entry dialog. If using a keyfile, the keyfiles salt length must be specified.
The default salt length is 256 bits. Any salt length entered must be a multiple of 8 bits.
By default, LibreCrypt will use the next available drive letter when opening a container.
This behaviour can be changed to use a specific drive letter on a container-by-container basis by setting it on this option.
The default setting here is "Use default"; use the next available drive letter
Note: If the chosen drive letter is in use at the time of opening, the next free drive letter will be used
Normally, a container's CDB will be stored as the first 512 bytes of the container.
However, this does increase the size of the container by the size of the CDB, which can make LibreCrypt containers more distinctive, and makes it slightly more obvious that a container file is a container file.
This is most clearly shown when creating a file based container: a 2GB container, for example, will be 2,147,484,160 bytes in length - made up of a 2,147,483,648 byte (2GB) encrypted disk image, plus a 512 byte embedded CDB.
To reduce this, it is possible to create a container without an embedded CDB; the CDB being stored in a separate file as a standard LibreCrypt keyfile.
In this case, a 2GB container would comprise of a 2,147,483,648 byte (2GB) encrypted disk image, plus a separate 512 byte keyfile which may be stored in a separate location to the container.
Note that if you store the container's CDB in a keyfile, you will always need to supply a keyfile when opening the container, and ensure that the "Data from offset includes CDB" advanced option shown on the LibreCrypt password entry dialog shown when opening must be unchecked after the keyfile is specified.
By default, LibreCrypt includes the CDB will be included as part of the container.
"Padding" is additional random data added to the end of the container file. Any padding added will not be available for use as part of the opened container, and serves to increase the size of the container.
Encrypted containers typically have a file size that is a multiple of 512 bytes, or a "signature size" beyond the last 1MB boundary. To prevent this, you may wish to append random "padding" data to the new container.
Padding also reduces the amount of information available to an attacker with respect to the maximum amount of the encrypted that may actually be held within the container.
When creating a new container the file or partition is first overwritten with psuedo-random data. This prevents any attacker from telling how much data is stored in the container and whether there is any hidden container. This data is known as "chaff".
Writing the 'chaff' can take some time - particularly with flash drives. Please see plausible deniability for details.
Note: This section only covers the password entry dialog shown when opening LibreCrypt containers. For opening Linux containers, please see the section on Linux containers.
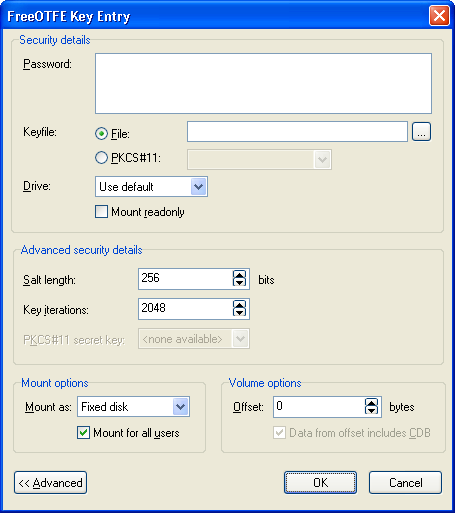
This should be set to the number of salt bits used in the PBKDF2 processing of the user's password, before using it to decrypt the container's CDB/keyfile being used.
By default, this is set to 256 bits - the same default length used when creating a new container.
This should be set to the number of key iterations used in the PBKDF2 processing of the user's password, before using it to decrypt the container's CDB/keyfile being used.
By default, this is set to 2048 iterations - the same default number used when creating a new container.
This option is only available if PKCS#11 support is enabled (see the section on Security Token/Smartcard Support for more information on how to use this setting).
LibreCrypt containers may be opened as any of the following types of virtual drive:
Usually, users should select removable disk.
Selecting the "removable disk" option causes the container to be opened as though it was a removable drive, e.g. a USB flash drive. For containers opened in this way, among other things, deleted files will not be moved to a "recycle bin" on the container, but will be deleted immediately.
By default, LibreCrypt opens containers as a removable disk.
If this option is checked, opened drives will be visible to all users logged onto the PC.
By default, this option is checked.
These options are intended for use with hidden containers, and containers which were created without a CDB embedded at the start of the container
When attempting to open a hidden volume, this should be set to the offset (in bytes) where the hidden container starts, as specified when creating it.
By default, this is set to an offset of 0 bytes.
This checkbox is only enabled if a keyfile has been specified.
If you are attempting to open either a hidden, or normal, container which was created without a CDB embedded at the start of the container, this checkbox should be changed so that it is unchecked.
For opening all other containers, this checkbox should be checked.
By default, this checkbox is checked.
The driver control dialog may be accessed by selecting "File | Drivers...". From here you may see all drivers installed, and their current state.
A summary of all available hash and cypher algorithms can be found by selecting "Help | List hashes..."/"Help | List cyphers...".
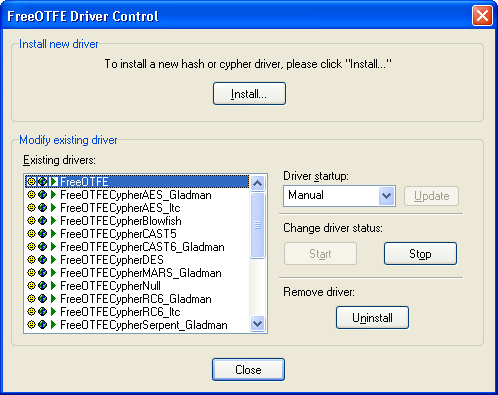 Driver control dialog
Driver control dialog
LibreCrypt drivers may be installed by clicking "Install...", and selecting the driver file to be installed.
LibreCrypt will then install the driver selected (adding it to the list of installed drivers), start it, and sets it to automatically start up whenever the PC boots up.
More than one driver can be installed at the same time by selecting holding down <SHIFT>/<CTRL> when selecting driver files in the "Open" dialog shown when "Install..." is clicked
The lower half of the Driver Control dialog lists all drivers currently installed, together with their status indicated with the icons listed below:
| Column | Icon | Description |
|---|---|---|
| Start up |  |
Driver must be started manually |
 |
Driver will be started automatically when the computer starts up | |
| Installation mode |  |
Driver is installed normally _ (no icon) _ |
 |
Driver is installed in portable mode _ (world icon)_ | |
| Status |  |
Driver started |
 |
Driver stopped |
After selecting an installed driver from the list, the operations listed below may be carried out on it:
Changes whether the selected driver is automatically started when the PC boots up. After changing this setting, click "Update" for the change to take effect.
The start/stop buttons start and stop the selected driver
Uninstalls the selected driver, and removes it from the drivers list.
When the user specifies a password for a new container, or changes an existing container's password, they have the option of carrying out analysis on the password entered in order to check it against a range of characteristics that are characteristic of weak passwords.
LibreCrypt includes a "password strength" meter.
This question applies to a future version of LibreCrypt.
Dictionary files (aka wordlist files) are straightforward text files which contain numerous words, one per line.
LibreCrypt and LibreCrypt Explorer can be configured to check passwords against such files, to filter out weak passwords.
LibreCrypt also supports wordlists in the Diceware (5 digit number, single space/tab, then word) and Mozilla Firefox (word followed by a single "/") formats.
Suitable dictionary files are widely available on the Internet; for example:
Dictionary/Wordlist