 LibreCrypt: Open-Source disk encryption for Windows
LibreCrypt: Open-Source disk encryption for Windows
 LibreCrypt: Open-Source disk encryption for Windows
LibreCrypt: Open-Source disk encryption for Windows
LibreCrypt supports all security tokens/smartcards (referred to as "tokens" in this documentation) which conform to the PKCS#11 (aka Cryptoki) standard, providing two factor authentication of LibreCrypt containers.
There are two ways in which tokens can be used:
In both cases case, the token's password (typically called a "PIN" - although not limited to numbers) is required in order for the token to be used.
These two methods can be used independently, or combined together.
In order to use tokens, LibreCrypt must first be configured to use the appropriate PKCS#11 library:
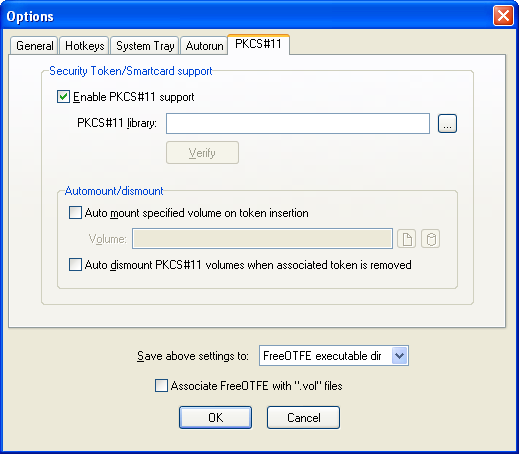
|
| Options dialog; PKCS#11 tab |
The menu-item under the "Tools" menu should then be enabled, as should the options (when appropriate) on the password entry dialog when mounting LibreCrypt containers
A list of driver library names supplied by common manufacturers may be found at Appendix E: PKCS#11 Driver Libraries
Keyfiles may be stored on tokens in a similar fashion to which they can be stored on (for example) a USB flash drive. However, unlike storing a keyfile on a USB flash drive, those stored on a token require the token's PIN to be entered before they can be accessed.
To add a keyfile to your token:
To use a keyfile stored on a token:
Note: More than one keyfile can be stored on a single token; however they must all have different names.
PKCS#11 tokens can also be used to add a further level of encryption to containers, by using the token to encrypt the container's CDB and/or keyfile(s).
The keys ("secret keys") used for this encryption are automatically generated by a token and can never be duplicated, extracted or in any way copied from the token, even if the token's PIN is known. All encryption/decryption operations used to secure a keyfile/container CDB are carried out by the token itself.
This mechanism therefore provides a means of "tying" a container/keyfile to a physical token; preventing it from being mounted unless the token is present and its PIN is known.
It should be noted however, that since it is inherent that no backups of the secret keys stored on a token can be made, the loss of the token will result in the loss of all data stored on the container it protects, unless a separate means of accessing the container (e.g. a keyfile which isn't secured by the same PKCS#11 token) is available.
To encrypt a container's CDB/keyfile:
It should be noted that the range of cyphers available for use is determined by the capabilities of your token, and not LibreCrypt * Click "OK" and the new key will be created
Click "Secure..."
In the dialog shown, specify the container/keyfile to be encrypted. If you are trying to secure a hidden container, enter the host container's filename/partition.
Note:
To use a container/keyfile which has been double-encrypted by a token:
LibreCrypt will only prompt you to enter your token's PIN as and when it's needed. LibreCrypt does not cache your PIN in any way
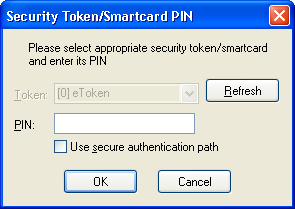
|
| PKCS#11 PIN entry |
The PIN entry prompt will display a list of all tokens found on your system, showing the slot number the token is inserted in, and the token's label. If you have not yet inserted your token, do so and click "Refresh" to refresh the list.
If only one token is found, it will be selected automatically, and the token selection control will be disabled. Otherwise, select the token you wish to use, enter your PIN, and click "OK" to continue.
If your token hardware features a secure authentication path (e.g. a smartcard reader with PIN entry keypad), you can take advantage of it by selecting the "Use secure authentication path" checkbox when LibreCrypt prompts for the token's PIN.